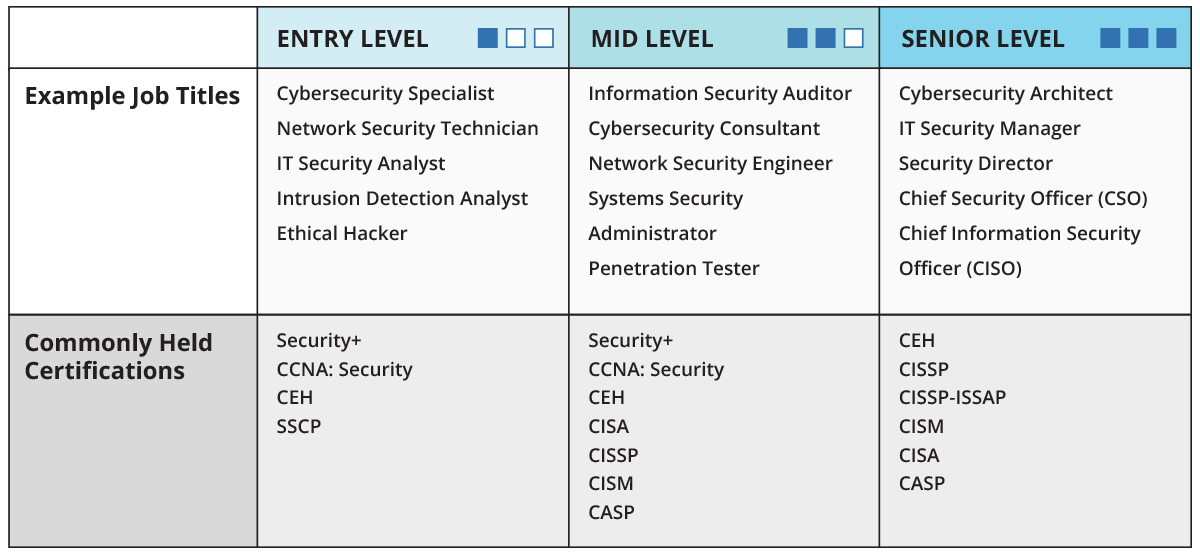
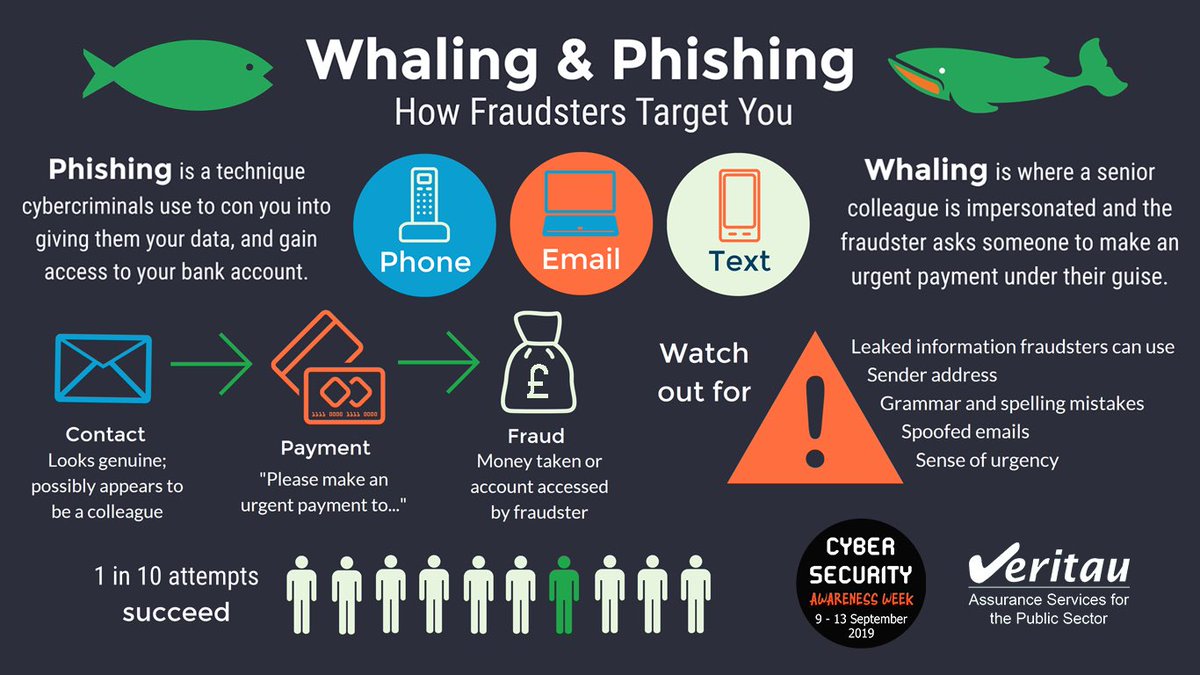
A whaling attack also known as whaling phishing or a whaling phishing attack is a specific type of phishing attack that targets high-profile employees such as the CEO or CFO in order to steal sensitive information from a company as those that hold higher positions within the company typically have complete access. A whaling attack is a method used by cybercriminals to masquerade as a senior player at an organization and directly target senior or other important individuals at an organization with the aim of stealing money or sensitive information or gaining access to their computer systems for.
 شافيق زيكري On Twitter 3 Whaling Whaling Ni Pula Jenis Spear Phishing Cuma Whaling Target Dia Ialah Orang Yang High Ranking Dalam Organisasi Macam Ceo Cfo Semua Tu So Whaling Lagi Berbaloi La
شافيق زيكري On Twitter 3 Whaling Whaling Ni Pula Jenis Spear Phishing Cuma Whaling Target Dia Ialah Orang Yang High Ranking Dalam Organisasi Macam Ceo Cfo Semua Tu So Whaling Lagi Berbaloi La
Next youll learn about whaling attacks and what to watch for.

What is whaling in cyber security. First youll learn about what exactly phishing is before moving on to the various methods of attacks and how to reduce your risk. Strengthen and Streamline Cybersecurity Across Multiplatform Environments. Phishing and Whaling you will learn how to protect yourself.
A whaling attack also known as whaling phishing or a whaling phishing attack. In this course Cyber Security Awareness. This could include financial information or employees personal information.
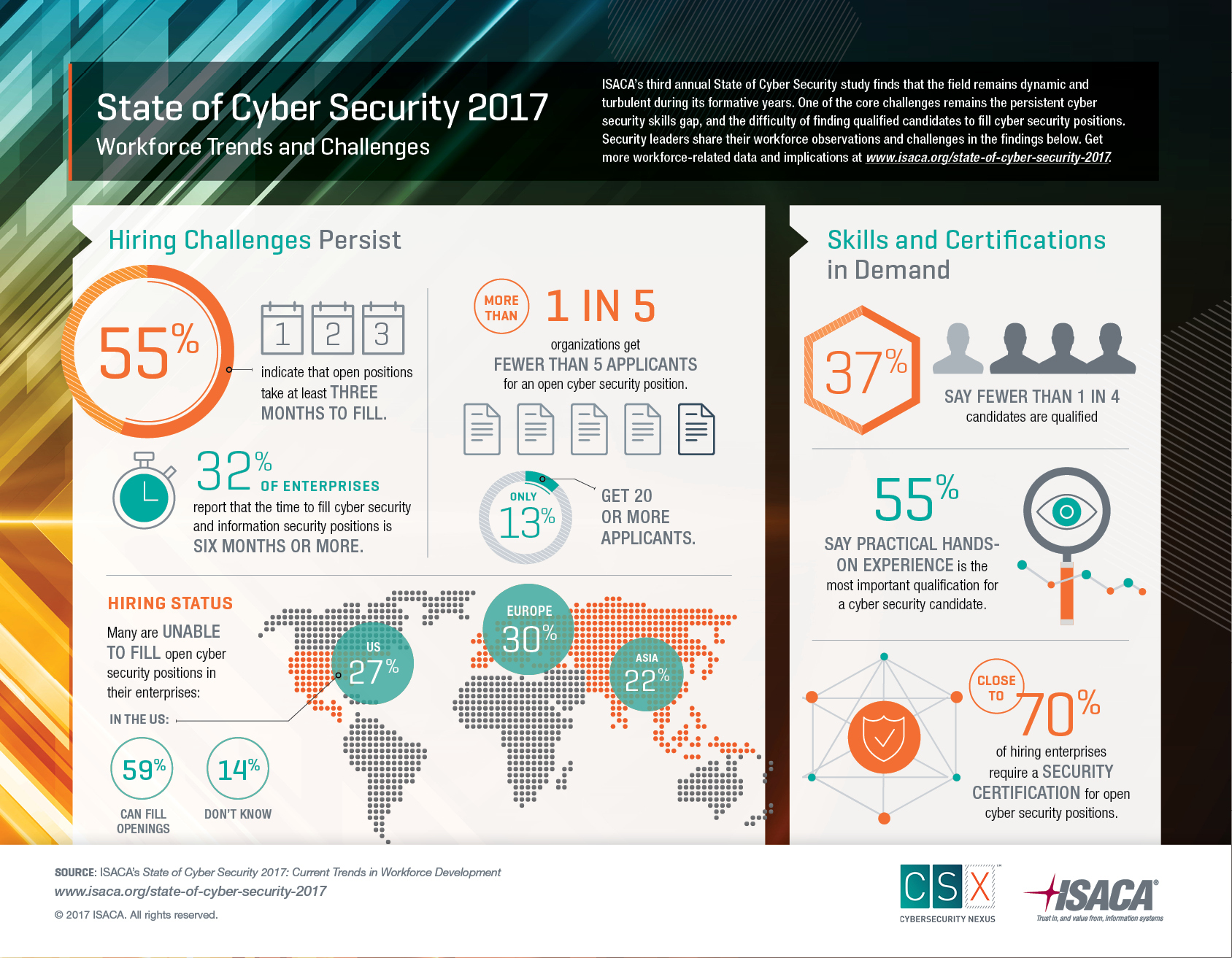
It occurs when an attacker masquerading as a trusted entity dupes a victim. As you might already know phishing attacks are usually broad large-scale cyberattacks in which hackers target a large number of users without any specific target in mind. Ad Microsoft Security Provides Integrated Security with Full Coverage.
In general phishing efforts are focused on collecting personal data about users. Since these types of targets are more likely to have access to confidential information the stakes can be much higher than a generic phishing attempt. A whaling attack also known as whaling phishing or a whaling phishing attack is a specific type of phishing attack that targets high-profile employees such as the chief executive officer or chief financial officer in order to steal sensitive information from a company.
What is whaling cyber attack. Whaling is a specific kind of malicious hacking within the more general category of phishing which involves hunting for data that can be used by the hacker. A whaling attack also known as whaling phishing is a specific type of phishing attack where scammers target the big fish in a company namely anyone in the c-suite such as CEO or COO.
Whaling is a form of phishing that targets high-profile executives managers etc. Ad Explore new cybersecurity trends technologies and approaches. A whaling attack is a type of phishing attack that targets high-level executives such as the CEO or CFO to steal sensitive information from a company.
Strengthen and Streamline Cybersecurity Across Multiplatform Environments. The methods used in a whaling attack are more sophisticated than those used in phishing. What is whaling in cybersecurity.
Phishing is a type of social engineering attack often used to steal user data including login credentials and credit card numbers. Whaling is a type of phishing attack specifically aimed at a high-profile target like a senior executive or a high-ranking government official. Together we can make networks devices and applications more secure.
Ad Microsoft Security Provides Integrated Security with Full Coverage. Also Know what is phishing attack in cyber security. Ad Explore new cybersecurity trends technologies and approaches.
A whaling phishing attack is defined as a cyber attack wherein cybercriminals disguise themselves as members of a senior management team or other high-power executives of an establishment to target individuals within the organization either to siphon off money or access sensitive information for malicious purposes. Whaling is a common cyber attack that occurs when an attacker utilizes spear phishing methods to go after a large high-profile target such as the c-suite. The term whaling comes from the size of attacks and the whale is picked because of.
Whaling is a type of phishing attack that hackers use to get access to information networks etc. Together we can make networks devices and applications more secure.