SWOT analyses are often praised for their simplicity you list the different variables on paper or in a SWOT Matrix ie. SWOT Analysis is instrumental in strategy formulation and selection.
:max_bytes(150000):strip_icc()/swot3-a5efa84709d24647ac8a88b556899f9c.png) Strength Weakness Opportunity And Threat Swot Analysis Definition
Strength Weakness Opportunity And Threat Swot Analysis Definition
You might perform this analysis for a product team organization leadership or other entities.
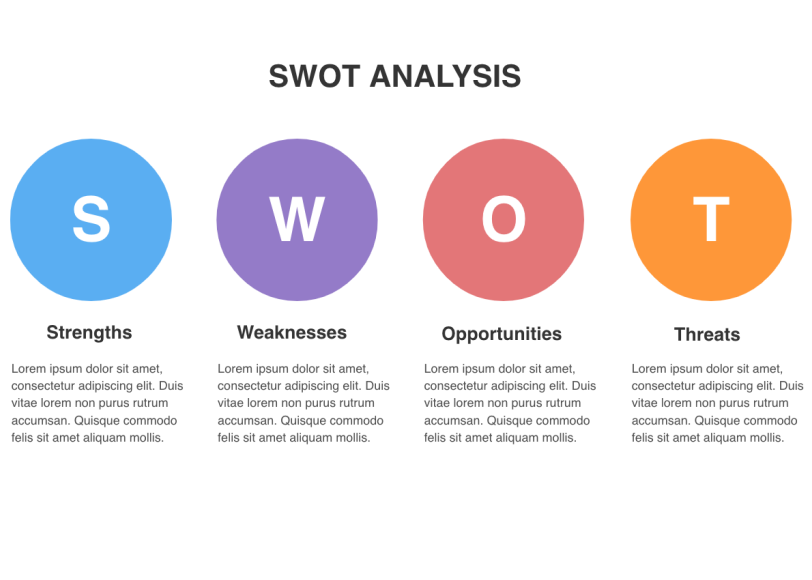
The swot analysis. A SWOT analysis is a way to evaluate strengths weaknesses opportunities and threats. Successful businesses build on their strengths correct their weakness. SWOT is an acronym for S trengths W eaknesses O pportunities and T hreats and is a structured planning method that evaluates those four elements of an organization project or business venture.
SWOT analyses are used in many business environments to gain a better understanding of how to plan for the future. Yet despite the tools wide use its often. It can be used to both assist with planning and as a way to quickly.
The SWOT analysis is a recognized tool to identify an organization department product or services strengths weaknesses opportunities and threats. A SWOT analysis is a simple but powerful. Theory SWOT is a strategic analytical tool for assessing strengths and weaknesses of a business analyzing opportunities available to the business as well as threats faced by the business.
A SWOT analysis is a compilation of your companys strengths weaknesses opportunities and threats. You can use SWOT Analysis to make the most of what youve got to your organizations best advantage. What Is a SWOT Analysis.
SWOT analysis is a technique developed at Stanford in the 1970s frequently used in strategic planning. SWOT strengths weaknesses opportunities and threats analysis is a framework used to evaluate a companys competitive position and to develop strategic planning. SWOT analysis can be used at organizational and personal levels.
The primary objective of a SWOT analysis is to help organizations develop a full awareness of. Weihrich is often recognized as the first person to identify the. What is a SWOT analysis and why should you use one.
S trength W eakness O pportunity T hreat. The SWOT analysis is a well-known popular and advantageous tool for providing qualitative information in an organized fashion. A SWOT analysis is an incredibly simple yet powerful tool to help you develop your business strategy whether youre building a startup or guiding an existing company.
SWOT stands for Strengths Weaknesses Opportunities and Threats and so a SWOT Analysis is a technique for assessing these four aspects of your business. SWOT stands for Strengths Weaknesses Opportunities and Threats. SWOT analysis is a decision matrix used by individuals or organizations to identify possible courses of action.
The matrix clearly defines the factors that will impact any course of action with each factor being categorized as a strength weakness opportunity or threat. A table and can make. SWOTs look at a combination of internal and external.
It is best when used as a guide and not as a prescription. What is a SWOT Analysis. It is a strong tool but it involves a great subjective element.
A SWOT analysis is a simple and practical form of evaluation model. What is a SWOT analysis. A SWOT analysis guides you to identify your organizations strengths and weaknesses S-W as well as broader opportunities and threats O-T.