Knowledge base of proven integrated principles practices and competencies for Lean Agile and DevOps. The worlds leading framework for business agility.
 Communities Of Practice Scaled Agile Framework
Communities Of Practice Scaled Agile Framework
Scaled Agile Framework SAFe for Lean Enterprises.

Community scaled agile. Purchase an Individual Membership you can learn more about purchasing an Individual. The scaled agile community is more than just a networking group. Portfolio SAFe Portfolio SAFe provides portfolio strategy and investment funding Agile portfolio operations and Lean governance.
Scaled Agile is moving to a membership model for the SAFe Community Platform going into effect in January 2021. Zen proverb adapted by John C. Its said that a wise person learns from his mistakes.
Role-based curriculum worldwide partner network global community. With this transition you will now be able to renew your membership at one of three tiers which will also include a bundle renewal of all your SAFe certifications. This group also has a LinkedIn presence to support sharing of knowledge and ideas with the Scaling Agile Community.
It supports building large integrated solutions that typically require hundreds of people to develop and maintain. The SAFe Community Platform offers a variety of tools to help you expand your knowledge of the Scaled Agile Framework SAFe manage your member account renew your certification and connect with other SAFe professionals. Founded by Scaled Agile the provider of SAFe Certifications the community was created to continue practitioners agile journey outside of the classroom.
A training and certification program was launched with the help of a small group of forward-looking early adopters. There are also regular events and. The scaled agile community is more than just a networking group.
This section contains articles authored by Scaled Agile. Full SAFe Full SAFe represents the most comprehensive configuration. Members can access forums workshop materials and refresher courses on-demand.
This group has been set up to share practice skills tools and techniques agile teams at scale. The primary reference for the scaled agile framework was originally the development of a big picture view of how work flowed from product management or other stakeholders through governance program and development teams out to customers. Guidance for organizing around value DevSecOps and agility for business teams.
There are 3 ways to become a member of the SAFe Community Platform. Communities of Practice - Scaled Agile Framework. This is a collection of our best public collaboration templates that are pre-packaged and ready for you to use.
Access tons of critical on-demand guidance for incorporating SAFe day to day tools to keep your business units and teams aligned and quantitative knowledge on how to improve within the Scaled Agile Community. But the wisest person of all learns from others successes. SAFe Collaborate is a cloud-based virtual workspace designed for the Scaled Agile Framework with templates to help you facilitate SAFe events like PI Planning feature prioritization participatory budgeting team retrospectives and more.
Take a course and be uploaded on a course roster either before or after you attend a course the timing of being uploaded to a course roster is at the discretion of your instructor 2. Access tons of critical on-demand guidance for incorporating SAFe day to day tools to keep your business units and teams aligned and quantitative knowledge on how to improve within the Scaled Agile Community. Evolving the Scaled Agile Framework.
SAFe Collaborate is a cloud-based virtual workspace designed for the Scaled Agile Framework with templates to help you facilitate SAFe events like PI Planning feature prioritization participatory budgeting team retrospectives and more. Configurable and scalable for Teams Programs and Portfolios. The second set Community Contributions contains content provided by the extended SAFe community.
A wiser one learns from others mistakes. Agile Architecture in SAFe Agile Contracts Agile Software. Members can access forums workshop materials and refresher courses on-demand.
Work Together Facilitate SAFe Events Via SAFe Collaborate. Just click on the template to get more information and start a forum. In 2011 it all came together.
What is the Scaled Agile Community. These articles are an integral part of the SAFe knowledge base. The Big Picture was christened as the Scaled Agile FrameworkSAFe for short.
Whats new in SAFe 5. Founded by Scaled Agile the provider of SAFe Certifications the community was created to continue practitioners agile journey outside of the classroom. Log in to access Communities of Practice professional development videos event information and other valuable resources.
Update to SAFe 5. The cadence for the meetup has changed through this time of.
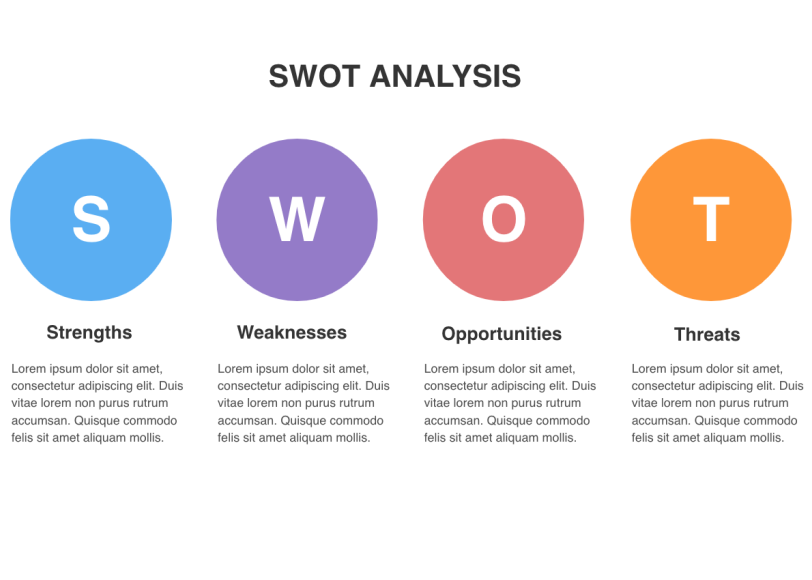
:max_bytes(150000):strip_icc()/swot3-a5efa84709d24647ac8a88b556899f9c.png)