If the content is already in that edge location CloudFront delivers it immediately. Including Computers Electronics Technology Arts Entertainment Science Education Games and 13 other categories.

888 USD for 10 TB.
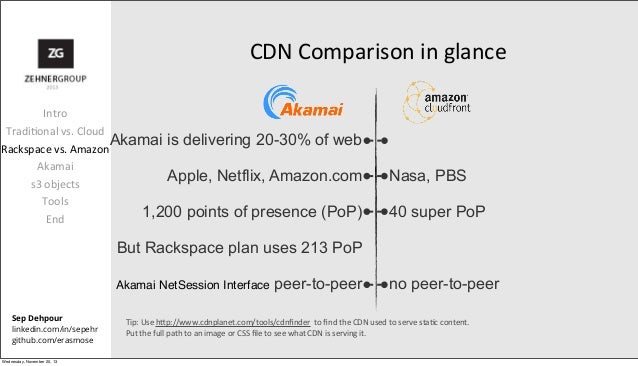
Akamai vs cloudfront. It only has 107 edge servers in five continents. Cloudflare is the global CDN which provides unique performance with a strong focus on security. 480 USD for 5 TB.
If the content is not currently in that edge location CloudFront retrieves it from an Amazon S3 bucket or an HTTP server. Akamai is ranked 7th in CDN while Amazon CloudFront is ranked 8th in CDN. On the other hand Akamai is considered to be the most popular CDN on the market.
CloudFront is the CDN of AWS Amazon Web Services the worlds largest cloud services provider. 24 USD for 250 GB. The company is actively involved in Lets Encrypt and is pushing HTTP2 adoption.
Despite its size this CDN has earned the trust of many high-profile clients including Pinterest Spotify Dropbox and. CloudFront is using Super PoP approach which means much fewer edge locations 54 as of January 2016 - see complete list here compared to the thousands that Akamai has around the world. Amazon CloudFront and Fastly seem to be favored by mainstream companies and overall well-known brands with a huge online presence while StackPath and CloudFlare cater to both the big boys and standard WordPress blogs or just entry-level websites.
Amazon CloudFront is not appropriate in case users can tolerate. When assessing the two solutions reviewers found Amazon CloudFront easier to use set up and administer. Akamai is rated 00 while Amazon CloudFront is rated 00.
In the last 12 months Akamai has a rating of 47 stars with 98 reviews while Cloudflare has a rating of 48 stars with 87 reviews. 48 USD for 500 GB. Requests for your content are automatically routed to the nearest edge location so content is delivered with the best possible performance.
It integrates with other Amazon Web Services products to give developers and businesses an easy way to accelerate content to end users with no minimum usage commitments. Reviewers also preferred doing business with Amazon CloudFront overall. Amazon CloudFront can be used to deliver your entire website including dynamic static streaming and interactive content using a global network of edge locations.
CloudFront is ranked 1st while Akamai is ranked 4th. Akamai is one of the oldest CDNs and generally considered to be the largest global CDN. 1 Amazon CloudFront has better usage coverage in more websites categories.
It is difficult to say who wins in CloudFlare vs CloudFront on the pricing front. Compared to Akamai CloudFront has a smaller network. Some stats here but no list of edge locations.
CloudFront is offered direct-to-customers through the Amazon Web Services. If you need help with the performance of your website the Akamai CDN offers an extensive suite of tools that may be beneficial to you. This is why CloudFront costs less than Akamai.
Jason you are mixing edge servers and edge locations which isnt very meaningful for example you might have 1000 servers in a single edge location. The company has a global infrastructure using high-performance equipment. Amazon CloudFront provides different plans for different content sizes.
Robert CloudFront can use custom origins as well. CloudFront can deliver dynamic static and streaming content. They have servers everywhere and a wide range of products and services.
Amazon CloudFront is a global content delivery network CDN service that accelerates delivery of your websites APIs video content or other web assets. Akamai vs Amazon CloudFront. In the question What are the best content delivery networks CDNs.
Reviewers felt that Amazon CloudFront meets the needs of their business better than Akamai. The most important reason people chose CloudFront is. Akamai is the oldest Content Delivery Network and recognized as the global CDN.
On the other hand Akamai is most compared with Cloudflare Imperva Incapsula Fastly Windows Azure CDN and Nokia Velocix Media Delivery Platform whereas Amazon CloudFront is most compared with AWS Global. They have widespread servers and. The CloudFront CDN can be easily integrated with WordPress which isnt always the case with Akamai.
They have servers everywhere and a wide range of products and services. Easy setup great cdn. Akamai is one of the oldest CDNs and generally considered to be the largest global CDN.
Solid documentation and APIs make CloudFront a developer-friendly CDN. If you pit CloudFlare vs MaxCDN MaxCDN looks like a much cheaper option with only 10 USD charged for 1 TB. 96 USD for 1 TB.
CloudFront offers a mature set of content delivery products and has a big network of POPs on many continents. 2 Akamai is leading in Vehicles Finance Jobs Career E-commerce Shopping and 3 other categories. Amazon CloudFront is best suited when there is a need of speed in serving static and dynanic web contents of a web application.
Be the first to leave a pro. Compare Akamai vs Cloudflare based on verified reviews from real users in the Web Application Firewalls market. The main difference between CloudFront and Akamai is the number of PoP servers.


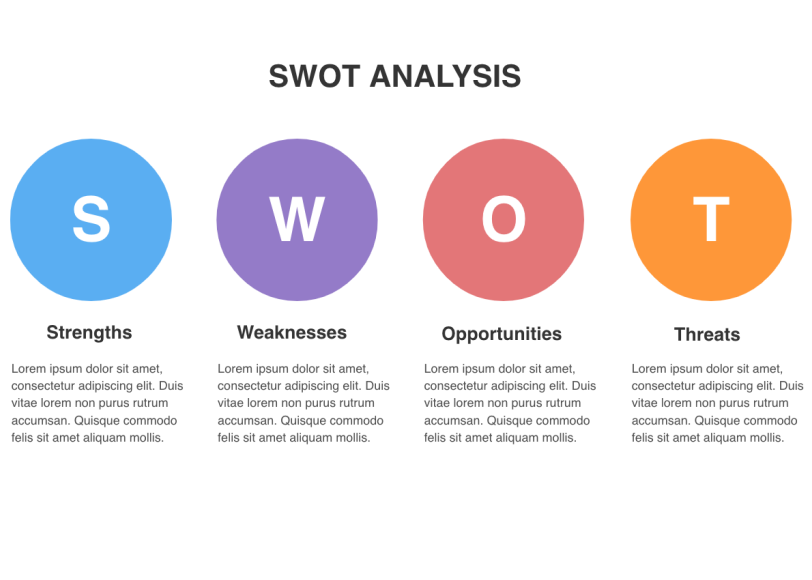
:max_bytes(150000):strip_icc()/swot3-a5efa84709d24647ac8a88b556899f9c.png)