Today security must be integrated into every fibre of the organization from HR implementing security awareness programs to legal ensuring regulatory compliance and the IT risk department monitoring threats all in an effort to become an enabler of secure business. Whether you have an outdated strategy in place or you are starting from scratch you can use this guide to get started building an effective and strategic cyber security plan.
 Cyber Security Strategy Ppt Powerpoint Presentation Infographic Template Portfolio Cpb Templates Powerpoint Presentation Slides Template Ppt Slides Presentation Graphics
Cyber Security Strategy Ppt Powerpoint Presentation Infographic Template Portfolio Cpb Templates Powerpoint Presentation Slides Template Ppt Slides Presentation Graphics
A comprehensive information security strategy considers people processes and technologies.
Information security strategy. Standardize processes in the security operations center SOC. A comprehensive cybersecurity strategy along with all the right cybersecurity tools are just part of the whole Information Security puzzle. People are often the weakest link in any organisations IS posture generally due to a lack of understanding on how they play a critical part in protecting your companys networks data and other.
A cyber security strategy is fundamental in helping your company take a proactive approach to security instead of reacting to every new threat which can be time consuming and expensive. Data breaches identity theft ransomware malware phishingall of us have been affected by the flood of security. Just think about it.
A program strategy provides guidance for how to make decisions and allocate resources to achieve overarching program objectives. When developing your security strategy for a hybrid or multi-cloud environment use these considerations. The most recent version of this strategy was.
Information security practices can help you secure your information ensuring that your secrets remain. Compare courses from top universities and online platforms for free. Information Security Strategy 2018-2023 51048 KB PDF The Chief Information Security Officer CISO is tasked with creating and managing the Universitys overall Information Security Strategy.
A formal security strategy is absolutely necessary. We define and keep the University information security system and associated policies and procedures up to date and fit for purpose and support departments and faculties to implement it. Our Strategy outlines some critical success factors.
It is far more effective to consider information security as a subset of a general business risk management policy. Ownership mandate and scope In order to build a functional and comprehensive cyber security strategy you need to have a mandate at the most senior level of the organisation. Compare courses from top universities and online platforms for free.
Holistic They consider the full spectrum of information security including people processes and technology. This means the Chief. This Informa on Security Strategy outlines the roadmap for the next 3 5 years by providing background details and highligh ng poten al threats and vulnerabili es that need to be iden fied assessed understood and countered.
A comprehensive security program includes both governance and management activities that utilize people processes and technologies to prevent. Risk aware They understand that security decisions should be made based on the security risks facing their organization not. We implement asset lifecycle management supporting the Universitys.
Having different processes for public and private clouds or for different public cloud environments can lead to. Do You Have a Strategy in Place Now. It answers the question of how you will evaluate the possible paths forward.
A strategy such as this means that your business takes an organised systemised approach to security. The most successful information security strategies are. Information Security InfoSec Strategy has broken free of the moorings that relegated the practice to a bunch of stereotypical nerdy administrators and analysts at least in our minds and it is now top of mind for thousands of companies large and small across the globe.
Ad Free comparison tool for finding Data Analysis courses online. The Information Security Strategy document outlines the current security landscape and plans to address it. The majority of incidents occur from within and result from employees being privy to sensitive information.
An information security program strategy is all about how. An information security strategy cannot be considered as a standalone policy. An information security strategy may include balanced implementation of some or all controls related to physical access system access authorization and approval of access to information based on business need background checks sharing with outside parties information flow within operations data retention backup and recovery security education and awareness training.
Information security InfoSec is critical to ensuring that your business and customer information is not manipulated lost or compromised. Fortunately cyber security strategy has an added plus in the form of deterring insider threats. Ad Free comparison tool for finding Data Analysis courses online.
 Information Security Analytics Blog Data Driven Security Strategy
Information Security Analytics Blog Data Driven Security Strategy
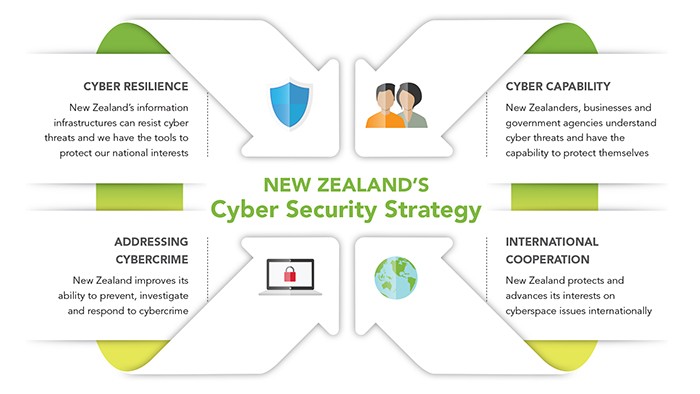 New Zealand S Cyber Security Strategy Department Of The Prime Minister And Cabinet Dpmc
New Zealand S Cyber Security Strategy Department Of The Prime Minister And Cabinet Dpmc
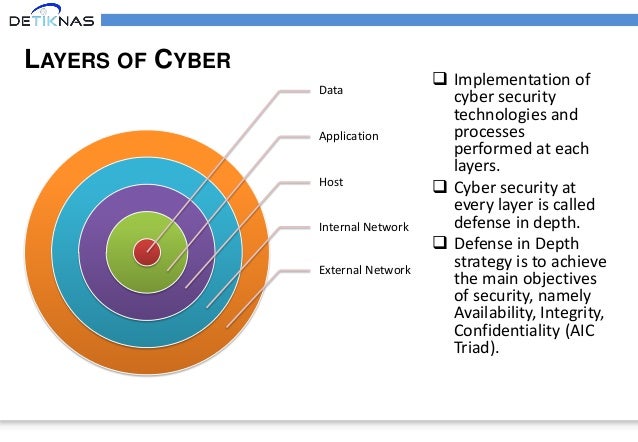 Indonesia National Cyber Security Strategy
Indonesia National Cyber Security Strategy
 Ian Jones Di Twitter Security Strategies Involve Both Cyber Security And Information Security Merged With Organizational Controls Via Fisher85m Egs Services Antgrasso Cybersecurity Strategy Transformation Infosec Https T Co Tqcgxdeqmx
Ian Jones Di Twitter Security Strategies Involve Both Cyber Security And Information Security Merged With Organizational Controls Via Fisher85m Egs Services Antgrasso Cybersecurity Strategy Transformation Infosec Https T Co Tqcgxdeqmx
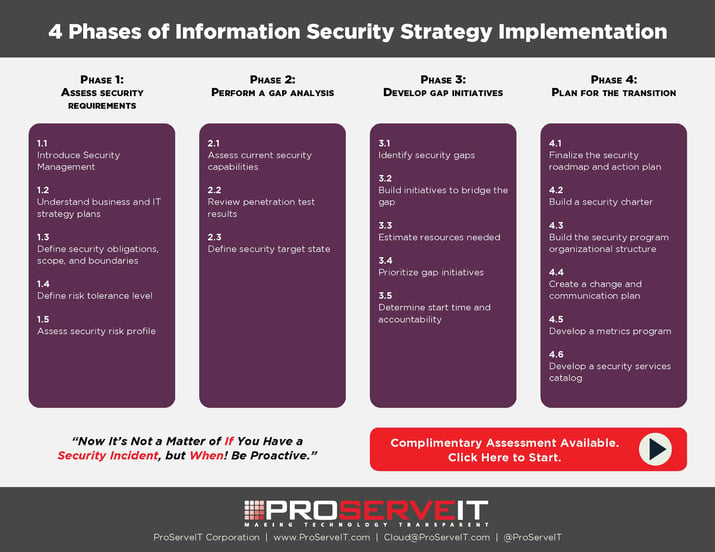
 Information Security Strategy Template February Ppt Download
Information Security Strategy Template February Ppt Download
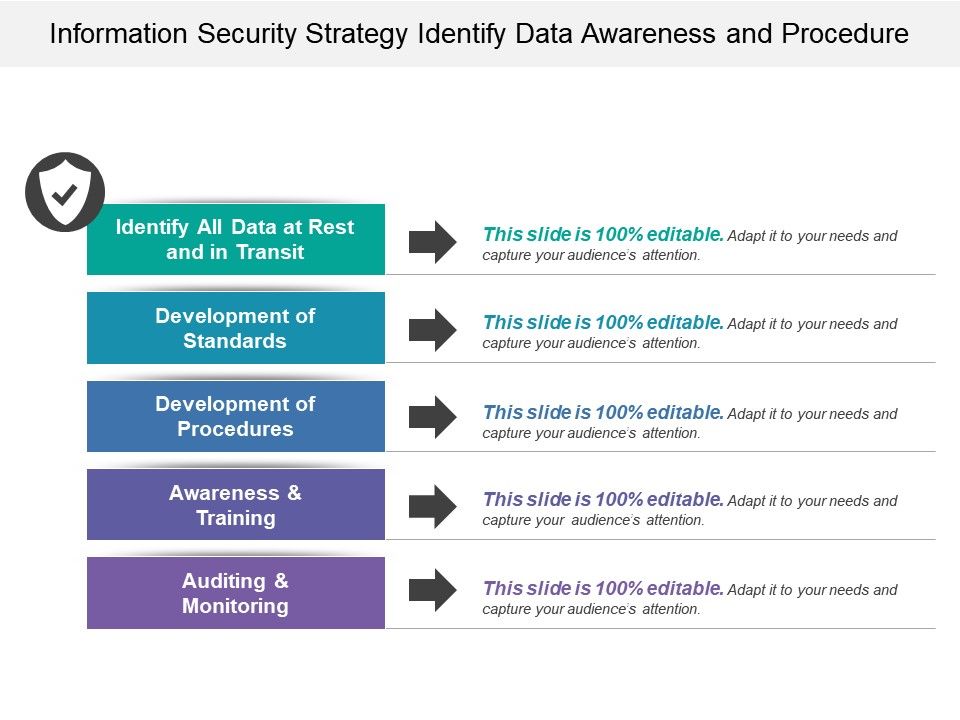 Information Security Strategy Identify Data Awareness And Procedure Presentation Powerpoint Templates Ppt Slide Templates Presentation Slides Design Idea
Information Security Strategy Identify Data Awareness And Procedure Presentation Powerpoint Templates Ppt Slide Templates Presentation Slides Design Idea
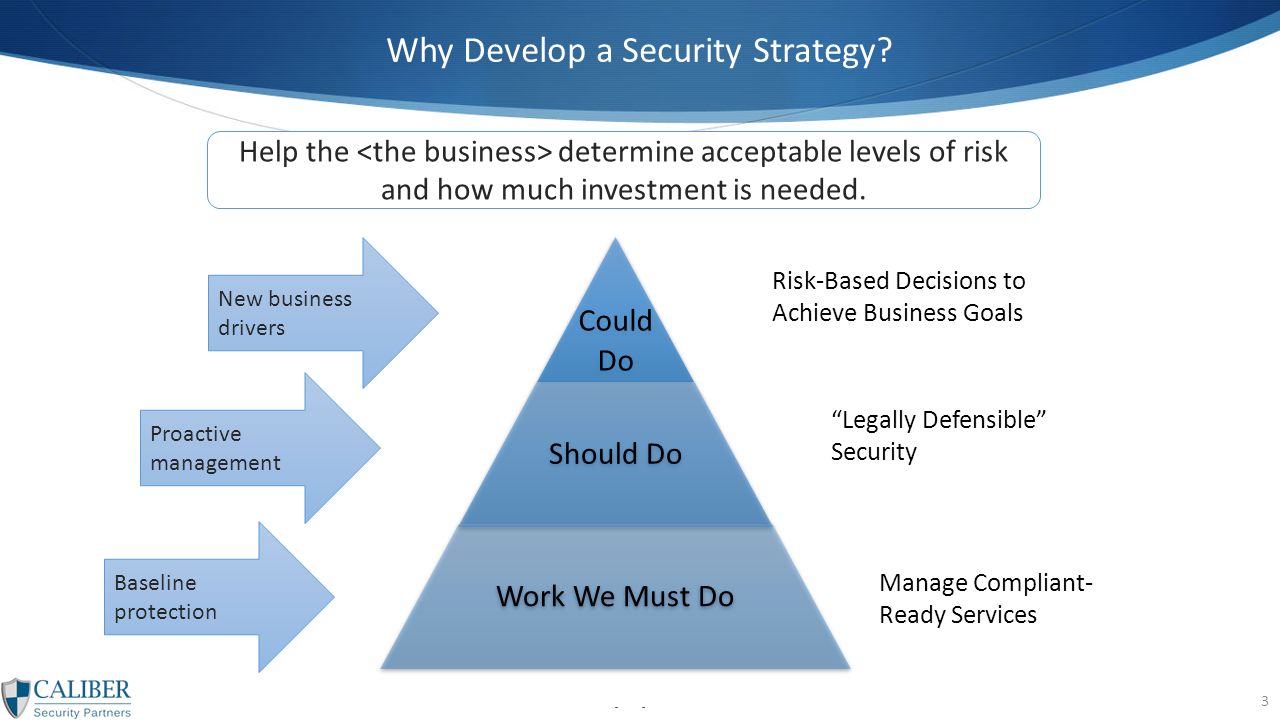
Defining A Security Strategy Why
 Information Security Strategy Governance Corix Partners
Information Security Strategy Governance Corix Partners
 2nd Enisa National Cyber Security Strategies Workshop Taking Place Today In Riga Enisa
2nd Enisa National Cyber Security Strategies Workshop Taking Place Today In Riga Enisa
 Information Security Strategy 3 Benefits And 3 Implementation Tips
Information Security Strategy 3 Benefits And 3 Implementation Tips
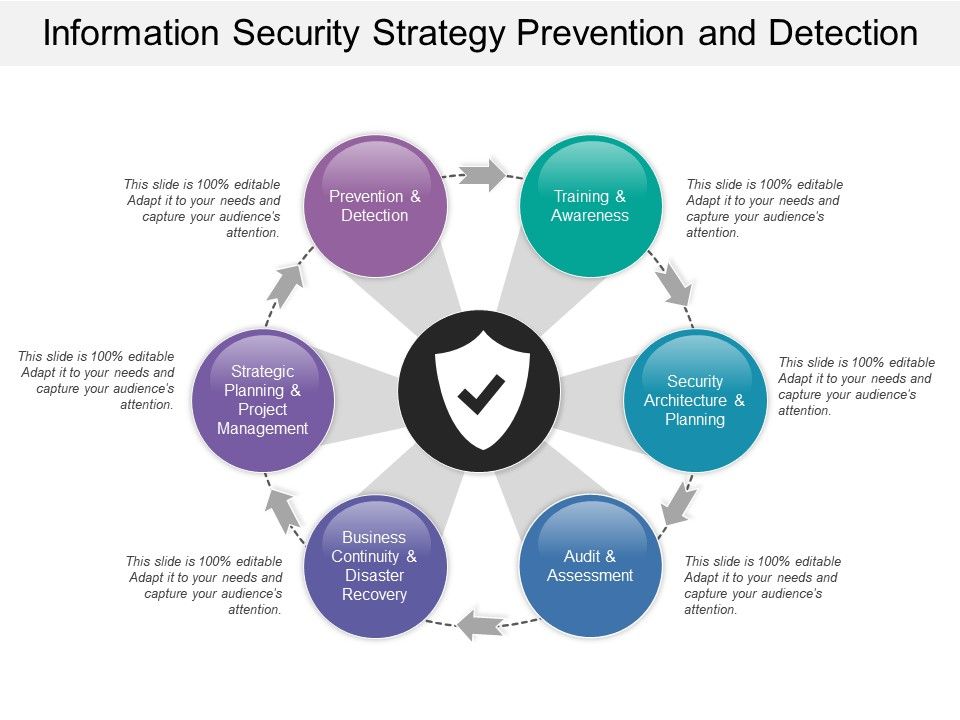 Information Security Strategy Prevention And Detection Powerpoint Templates Backgrounds Template Ppt Graphics Presentation Themes Templates
Information Security Strategy Prevention And Detection Powerpoint Templates Backgrounds Template Ppt Graphics Presentation Themes Templates
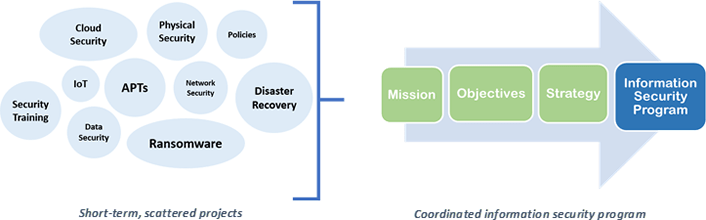 Creating An Information Security Strategy For Higher Education Vantage Technology Consulting Group
Creating An Information Security Strategy For Higher Education Vantage Technology Consulting Group
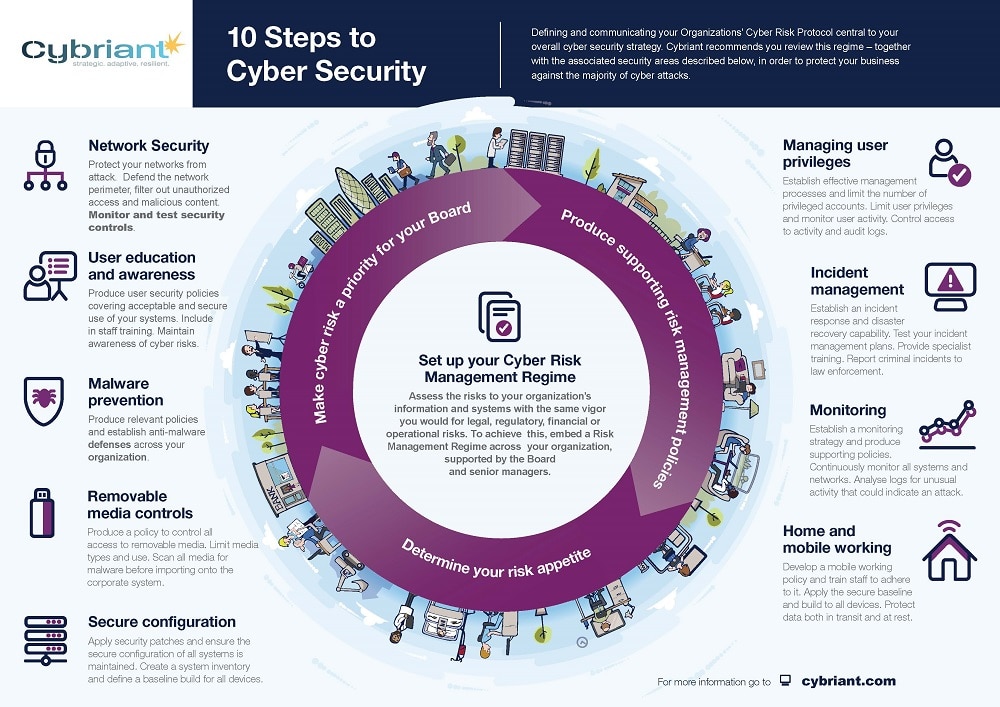 Upgrade Your Cyber Security Strategy With These 10 Steps Cybriant
Upgrade Your Cyber Security Strategy With These 10 Steps Cybriant

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.