This paper deals wit. In the View drop-down menu Used By is licensed as part of the Management Pack Plus for Identity Management.
How To Use Oauth For Enterprise Identity Management
IPsec Internet Protocol Security IPsec Internet Protocol Security is a suite of.
Enterprise identity management. To do this the project will improve how the university uniquely identifies every student instructor researcher. Identity data is among the most complex and sensitive information for any enterprise. Identity and access management IAM in enterprise IT is about defining and managing the roles and access privileges of individual network entities users.
The complex part of the answers takes the rest of this document. All features functions links buttons and drill-downs on this menu are licensed as part of the Management Pack Plus for Identity Management. From the Enterprise menu select Configuration and Topology Customization.
Oracle Enterprise Identity Management is highly customizable and can be deployed as software on-premises or as an Oracle Cloud Infrastructure instance. With more than 70000 users who interact with university systems more than 6 million times a year Enterprise Identity Management EIM aims to improve user experience and manage risk associated with this incredible volume. Identity and access management is a multistep process that involves careful planning for identity integration and other security considerations such as blocking legacy authentication and planning for modern passwords.
The mass migration to Remote Workforce enterprise operations has created more Security Gaps and Risks than ever before. It enables secure access for employees contractors partners and customers allowing companies to deploy workloads on their infrastructure provider of choice while enabling all modes of access. Identity management is everything that deals with managing identities in the cyberspace.
EIM will improve the experience of every instructor researcher student employee alum donor and visitor whether they are requesting a business system report or an annual parking permit. Managing users and groups is fundamental to identity and access management. Any application - mobile web enterprise - written with any framework.
Enterprise identity management IdM or ID management is the part of identity and access management systems IAM responsible for identifying authenticating and authorizing employees and their use of corporate information technology resourcesThe second part of IAM access management works in conjunction with identity management to ensure employees have access to. At its core user and group management consists of creating and updating identities and setting rules for the resources each user identity can access. Single Pane of Glass for Enterprise Identity Management.
CMS Identity Management CMS Identity Management IDM system is an established enterprise-wide identity management solution. IDM is leveraged by CMS business applications across the agency. With just a few lines of code you can implement secure comprehensive identity management.
End users of all business applications that integrate with this solution can use a single set of user credentials to access any integrated application. The easy part is. Its also turbulent handling invidual changes organizational changes affiliates and VIPs personal changes such as new legal names and even societal changes.
Bring yourself up to speed with our introductory content. About Enterprise Identity Management EIM There are currently more than 70000 users who interact with university systems more than 6 million times a year. Enterprise identity and access management helps firms decrease costs and enhance productivity across the board by streamlining their processes for enterprise identity and access management providers the overarching goal is to grant access to the right enterprise assets to the right users in the right context from a users system.
Enterprise identity and access management Get Started. Auth0 is a universal identity clearinghouse. And any Identity Provider IdP from popular social sites to enterprise IdPs like Active Directory SAML and legacy databases.
Answer to that question is both easy and very complex. Over 74 of all breaches involve Access to a Privileged Account. Staging planning also involves selection of business-to-business or business-to-consumer identity and access management.
It also includes assigning sets of users to groups for efficient management.
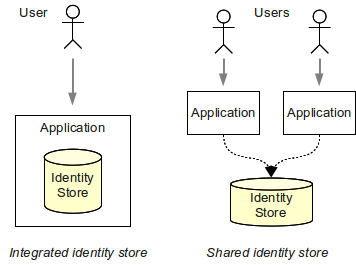 Enterprise Identity And Access Management Evolveum Docs
Enterprise Identity And Access Management Evolveum Docs
 Enterprise Application Security And Identity Management
Enterprise Application Security And Identity Management
 Identity And Access Management Enterprise Identity Management Zencc
Identity And Access Management Enterprise Identity Management Zencc
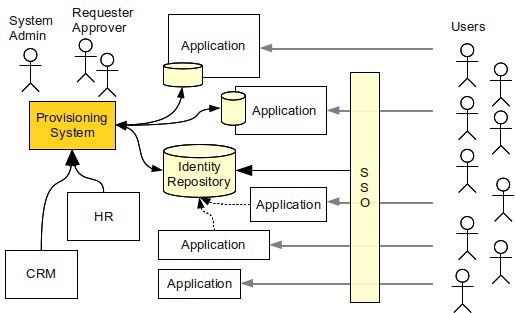 Enterprise Identity And Access Management Evolveum Docs
Enterprise Identity And Access Management Evolveum Docs
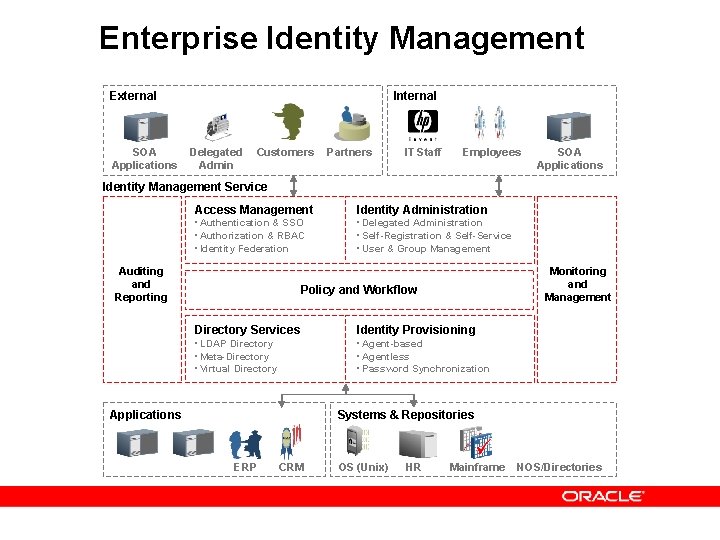 Oracle Identity And Access Management Suite Rafael Torres
Oracle Identity And Access Management Suite Rafael Torres
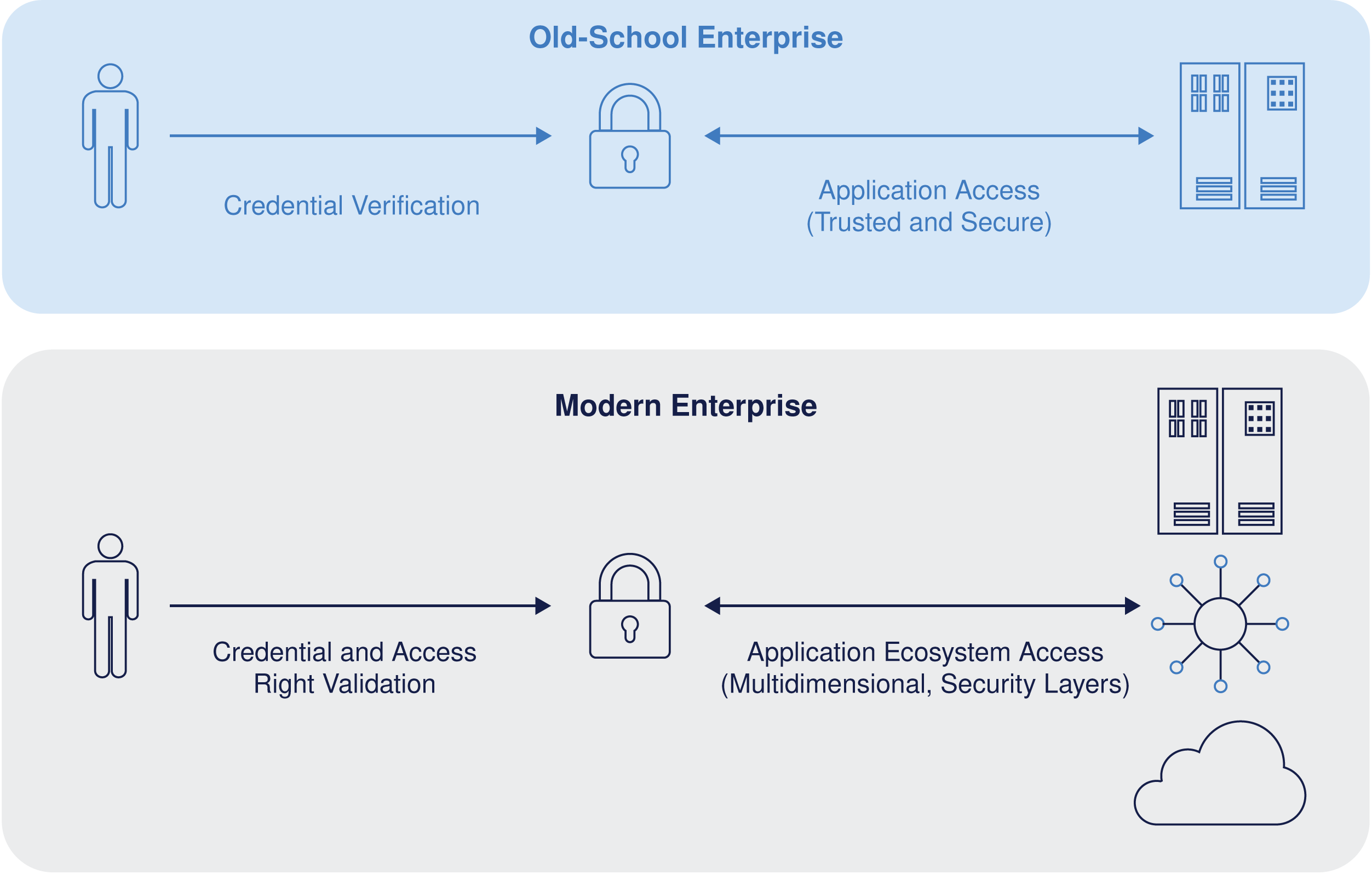 Counter Identity Driven Threats With Identity Analytics And Intelligence By Securonix Medium
Counter Identity Driven Threats With Identity Analytics And Intelligence By Securonix Medium

 Assessing The Value Of Enterprise Identity Management Eidm Towards A Generic Evaluation Approach Semantic Scholar
Assessing The Value Of Enterprise Identity Management Eidm Towards A Generic Evaluation Approach Semantic Scholar
What Is Enterprise Identity Management Quora
 What Is Enterprise Identity And Access Management By James Smith Saaspass
What Is Enterprise Identity And Access Management By James Smith Saaspass
 Enterprise Identity Management Towards An Investment Decision Support Approach Denis Royer Springer
Enterprise Identity Management Towards An Investment Decision Support Approach Denis Royer Springer
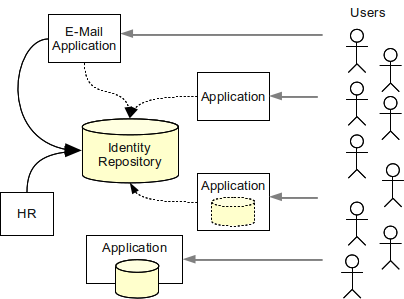 Enterprise Identity And Access Management Evolveum Docs
Enterprise Identity And Access Management Evolveum Docs
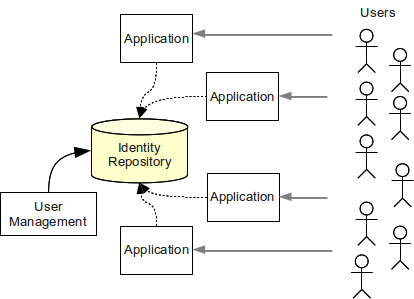 Enterprise Identity And Access Management Evolveum Docs
Enterprise Identity And Access Management Evolveum Docs
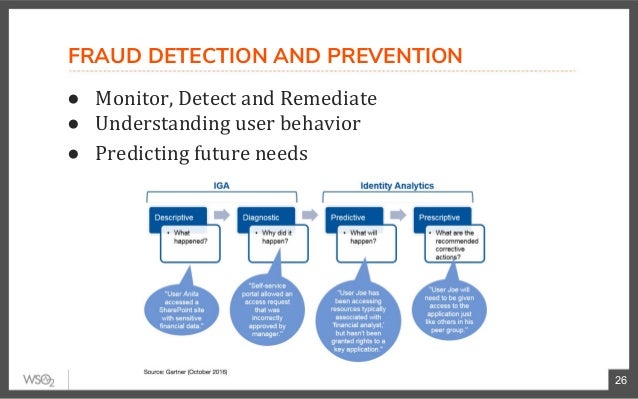 Enterprise Identity And Access Management Use Cases
Enterprise Identity And Access Management Use Cases

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.